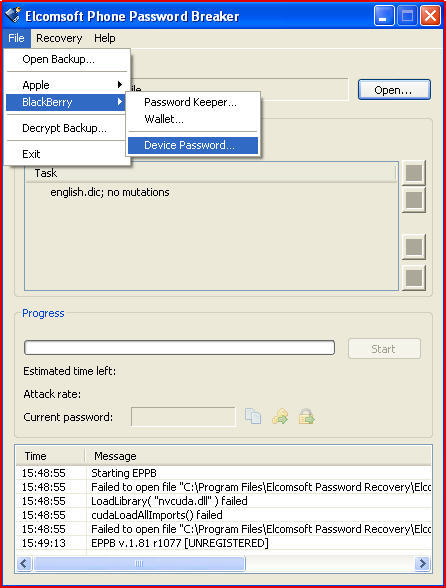
- Elcomsoft Phone Password Breaker
- Elcomsoft Internet Password Breaker
- Elcomsoft Phone Breaker Free Download
Decrypt Mac OS Keychain
Elcomsoft Phone Breaker enables forensic access to password-protected backups for smartphones and portable devices based on RIM BlackBerry and Apple iOS platforms. The password recovery tool supports all Blackberry smartphones as well as Apple devices running iOS, including iPhone, iPad and iPod Touch devices of all generations released to date, including the iPhone 6 Plus and iOS 8.
- 9.15 Shareware; Access protected backups of BlackBerry, iPhone, iPad and iPod! Elcomsoft Phone Password Breaker with support for all BlackBerry smartphones and Apple mobile devices.
- Having the user’s Apple ID password, experts can use Elcomsoft Phone Breaker to download cloud backups created by user’s iOS devices such as iPhone and iPad from Apple iCloud. Over-the-air acquisition produces a clean, unencrypted backup that can be viewed in Elcomsoft Phone Viewer or analyzed in one of the many commercial forensic tools.
Elcomsoft Password Digger is a Windows tool for decrypting the content of system and user keychains pulled from a Mac OS computer. The tool exports the full data set into an XML file or builds a filtered dictionary for using with password recovery tools. The system and all user keychains can be decrypted.
Elcomsoft Password Digger enables access to highly sensitive information including Wi-Fi passwords, user’s Apple ID and iTunes passwords, Web site and email account passwords, as well as other sensitive information.
Using Elcomsoft Password Digger together with other ElcomSoft tools opens a way to download iCloud backups created by the user’s iPhone or iPad (via Elcomsoft Phone Breaker), and offers a better chance of breaking other passwords faster by generating a custom dictionary (via Elcomsoft Distributed Password Recovery).
Extract macOS Passwords. Build Custom Dictionary
Elcomsoft Password Digger offers a one-click tool to automatically extract all relevant passwords and save them into a filtered, plain-text dictionary.
Attacking many types of passwords is impossible without a quality dictionary. Even with GPU acceleration, certain types of passwords (such as those protecting Microsoft Office 2010-2013 documents) are just too slow to brute force. A custom dictionary containing the user’s other passwords is invaluable in assisting these types of attacks. By reviewing a list of user’s passwords, experts may be able to derive a common pattern, creating a set of rules for the password recovery tool.
Brute-forcing Microsoft Office 2010 passwords can take ages even with GPU acceleration
Elcomsoft Password Digger can produce highly relevant password dictionaries in one click. By extracting all passwords stored in the user’s keychain and saving them into a plain, filtered text file that only contains the passwords, Elcomsoft Password Digger allows building a highly relevant custom dictionary for breaking strong passwords. The resulting file can be used for dictionary attacks with Elcomsoft Distributed Password Recovery, Elcomsoft Password Recovery Bundle, as well as with individual password recovery tools.
Extract Keychain Data
In order to use Elcomsoft Password Digger, experts will need a Windows PC, keychain files extracted from Mac OS, as well as the user’s authentication information (Mac OS login and password or keychain password, if it’s different). For decrypting system keychains, the tool will require a decryption key that must be extracted from the Mac OS computer (administrative privileges are required to extract the file from a live system).
System Keychain
- Keychain file extracted from the user’s Mac OS system
- Decryption key from the same system [1]
User Keychain
- Keychain file extracted from the user’s Mac OS system
- User’s local login password or keychain password (if different)
Features and Benefits
- Gain access to encrypted information stored in Mac OS keychain
- Use extracted Apple ID password to download iCloud backups (with Elcomsoft Phone Breaker)
- Decrypt system and all user keychains obtained from the Mac OS system
- Considerable time savings compared to using Apple Keychain Access
- Export full keychain data into an unencrypted XML file
- Speed up password recovery by producing filtered plain-text files to be used as custom dictionary (with Elcomsoft Distributed Password Recovery and other tools)
The decryption key for system keychain must be extracted; administrative privileges are required if extracting from a live system
Category: «Did you know that...?», «Elcomsoft News», «Security», «Tips & Tricks»
22 9 - 31
Who am I to tell you to use two-factor authentication on all accounts that support it? This recommendation coming from someone whose business is supplying law enforcement with tools helping them do their job might be taken with a grain of salt by an average consumer. Yet we still strongly believe that, however good a password you have to encrypt your local documents or NAS drives, any remotely popular online service absolutely requires an additional authentication factor.
We covered the risks related to passwords more than once. There is no lack of horror stories floating on the Internet, ranging from leaking private photos to suddenly losing access to all data and devices registered on a certain account. Today, smartphones store excessive amounts of information. If any of that data is synced with a cloud, the data will be shared with something other than just your device.
So what is that “other” thing that you need to secure access to your account? It might be something you have in addition to something you know. Something that cannot be easily stolen or accessed remotely. This is exactly what two-factor authentication is for.
All three major mobile companies, Apple, Google and Microsoft, offer very different implementations of two-factor authentication. Speaking Google, you have several convenient options: SMS (which is not really secure, and Google knows it), the recently added Google Prompt, the classic Google Authenticator app, printable backup codes, FIDO keys and a few more. (Spoiler: if you are on a different side and need to extract the data as opposed to protecting it, we have an app for that).
What about Apple? There are a few things you should definitely know about Apple’s implementation. The problem with Apple is that Apple accounts protected with two-factor authentication can be actually less secure at some points. Surprised? Keep reading.
Take Over That Person’s Account by Resetting Their iCloud Password
If I get a dollar every time when asked how to reset iCloud password… Oh, wait; I will sure become a billionaire soon!
Jokes aside, resetting iCloud password has many legitimate purposes other than reusing a stolen iPhone. Sometimes the password can be extracted from different sources, but what if all known methods failed?
Neatly every system allows resetting the password if it is lost or forgotten. You just need to prove that you are you, the account owner; or have a legal right to access it.
Here is how it worked with Apple iCloud in “pre-2FA” times. You could reset your password through email, or by correctly answering the security questions. If you did not have access to your mail account anymore, forgot about your security questions, and somehow lost access to the trusted phone number, there was still an option of going through Apple support. While that could take a long time and may require telling Apple your personal data, such as a credit card. All these methods are described in Apple knowledge base:
Instructions are a bit confusing, but we wanted to concentrate on just a single case: if you have two-factor authentication enabled and have the passcode set.
Elcomsoft Phone Password Breaker
We made a video for you (note: iOS 10 or later is required, 2FA should be enabled on the account, and the device should be passcode protected with a known passcode):
So all you have to do is just couple of clicks on the trusted iPhone, and you’ll have to enter a passcode once.
What Apple does not mention is that the passcode is not always required. We cannot say for sure, but it seems that the requirement to enter the passcode here is eliminated if the iPhone has been unlocked with it (but not Touch ID or Face ID) last time, or if that feature (changing the iCloud password) has been already used. After some time, however, you will be still prompted for the passcode – is it cached, or may be the special token is created? No idea.
What if you do not have an iPhone handy, but only have a Mac? It’s almost the same. Go to iCloud settings, and there you can set the new password without entering the old one. All you will be prompted for is the password you use to log in into your Mac.
(as a side note, that works the opposite way as well, i.e. you can reset Mac login password through the iCloud, but that’s a different story)
Is it a bug? Definitely not, it is in fact a convenience feature. But if you ask whether if creates a security risk, the answer is a reassuring “Yes”. All you need is a trusted device and the passcode (or a Mac password). Pease also note that the Mac password can be cracked (though not very easy); we have an app for that, too.
What if 2FA is not enabled on the account, or passcode (or login password in a case of Mac) is not set? You will be prompted for the old password (and sometimes even forced to answer security questions). But what if we enable 2FA or set the passcode first? No, that will not work either, try yourself and see what happens.
Eliminating the Second Factor
There was always just one workaround to access iCloud accounts protected with 2FA: using tokens instead of a password. We were the first who discovered it a long time ago, and it was a real breakthrough in iCloud acquisition.
Apple’s response was smart: they dramatically shortened the token’s lifetime. The token extracted from the desktop still works for most types of iCloud data, including files in iCloud Drive, iCloud Media Library and synced information (contacts, call logs, calendars, notes and Safari browsing history). However, if you try to use that token to download iCloud backups the next day, you can only obtain the list of devices and backups, but downloading fails.
The token extracted from the desktop is not the only one that we use. If you log on into 2FA-protected iCloud with Phone Breaker using a password, you are of course prompted for the second authentication factor as well. This could be a code send to the trusted device as a push notification, or a code generated on the device manually, or (now with the latest version) a code delivered to a trusted phone number as a text message (SMS). If the login was successful, EPB creates and saves its own token, and for all future requests to the same account make use of that token instead; this allows logging in without providing the second factor.
But again, the problem is with token expiration.
The solution? We have it now. And surprisingly, it uses the good old password (so the new token is generated every time), but does not require you to enter the second factor.
How could that be possible? Thanks to Apple’s new authentication scheme, GSA (GrandSlam Authentication) available in iOS 9+, macOS 10.11 and later. With this, one can use SMS to receive the security code. More importantly, this makes the computer “trusted”, so it does not ask for the second factor anymore.
Elcomsoft Internet Password Breaker
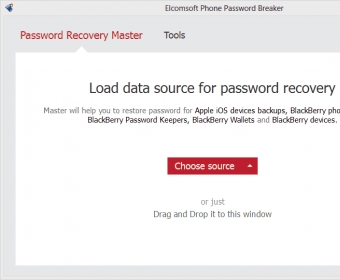
This means that if you run Elcomsoft Phone Breaker 8.1 on the computer that is already logged into the cloud (the suspect’s computer), then all you need is a password to the account. That will be it! No push notification to the trusted devices, no SMS codes, nothing. And if you run EPB on another desktop, you will only have to provide the second factor once, and we will do the rest of the job (make the computer trusted) for you – but, in contrary to the token-based solution, no problems with expiration anymore. Of course, we will also save the password for you, so to get fresh portion of iCloud data, you only need to select the Apple ID from the list.
What about iCloud Keychain? About the same. No 2FA anymore, just login and password
Can we get data that makes the computer trusted and move it to another computer? Not at this time, but we are working on it. It is not as easy as copying a file; we’re still trying to figure out what exactly makes the computer “trusted”.
2FA: the Good, the Bad and the Ugly
So let’s sum it all up.
- With iOS 10+, you can easily change the iCloud password even if you don’t know the original one. This goes directly from the device (iPhone, iPad, Mac etc.) All you need is the device passcode (or Mac system password); sometimes it can even be done without the passcode.
- The iCloud Keychain is always stored in the cloud (not just synced across devices as would be possible without two-factor authentication). Theoretically, it is accessible by TLA. There is no further protection such as the special iCloud Security Code (as with accounts without 2FA).
- The second factor is not required if you run Elcomsoft Phone Breaker 8.1 on a “trusted” computer. If you do not have access to a trusted computer (the one where the given account is already being used by the system), we can make any computer trusted by passing 2FA just once. There will be no token expiration problem here; iCloud backups can be downloaded any time further.
All this is definitely good news for the forensic experts. How this can affect your personal security and privacy? You decide.
Elcomsoft Phone Breaker Free Download
22 9 - 31
